对于Blutter的安装配置
首先从Github上下载一个 Blutter 作为 Flutter 的反编译工具
cd .\blutter\
python .\scripts\init_env_win.py
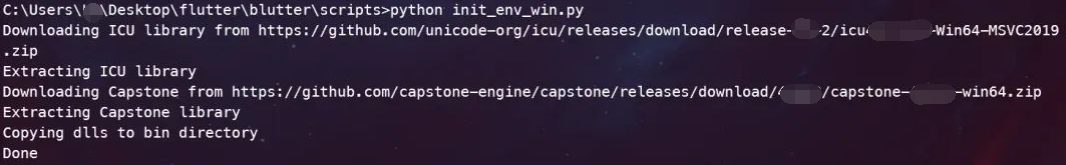
然后使用x64Native Tools Command Prompt for VS 2022

在Blutter反编译的过程中有报错
D:\blutter-main>python blutter.py C:\Users\Aar0n\Desktop\Challenge\NKCTF\2024\inputtttt\inputtttt-new\lib\arm64-v8a ./output
Dart version: 3.4.0-190.0.dev, Snapshot: 75f170bc3de3cc2026e3e159bef60351, Target: android arm64
flags: product no-code_comments dwarf_stack_traces_mode no-lazy_dispatchers dedup_instructions no-tsan no-asserts arm64 android compressed-pointers null-safety
-- Configuring done (0.0s)
-- Generating done (0.0s)
-- Build files have been written to: D:/blutter-main/build/blutter_dartvm3.4.0-190.0.dev_android_arm64
[1/1] Linking CXX executable blutter_dartvm3.4.0-190.0.dev_android_arm64.exe
FAILED: blutter_dartvm3.4.0-190.0.dev_android_arm64.exe
C:\WINDOWS\system32\cmd.exe /C "cd . && D:\Cmake\bin\cmake.exe -E vs_link_exe --intdir=CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir --rc="D:\Windows Kits\10\bin\10.0.22621.0\x64\rc.exe" --mt="D:\Windows Kits\10\bin\10.0.22621.0\x64\mt.exe" --manifests -- "D:\Visual Studio\2022\Community\VC\Tools\MSVC\14.37.32822\bin\Hostx64\x64\link.exe" /nologo CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\cmake_pch.cxx.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\CodeAnalyzer.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\CodeAnalyzer_arm64.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartApp.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartClass.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartDumper.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartField.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartFunction.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartLibrary.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartLoader.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartStub.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartThreadInfo.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartTypes.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Disassembler.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Disassembler_arm64.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\ElfHelper.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\FridaWriter.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Util.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\VarValue.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\il.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\main.cpp.obj /out:blutter_dartvm3.4.0-190.0.dev_android_arm64.exe /implib:blutter_dartvm3.4.0-190.0.dev_android_arm64.lib /pdb:blutter_dartvm3.4.0-190.0.dev_android_arm64.pdb /version:0.0 /machine:x64 /INCREMENTAL:NO /subsystem:console /LTCG /OPT:REF /OPT:ICF D:\blutter-main\packages\lib\dartvm3.4.0-190.0.dev_android_arm64.lib D:\blutter-main\blutter\..\external\capstone\capstone_dll.lib D:\blutter-main\external\icu-windows\lib64\icuuc.lib kernel32.lib user32.lib gdi32.lib winspool.lib shell32.lib ole32.lib oleaut32.lib uuid.lib comdlg32.lib advapi32.lib && cd ."
LINK: command "D:\Visual Studio\2022\Community\VC\Tools\MSVC\14.37.32822\bin\Hostx64\x64\link.exe /nologo CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\cmake_pch.cxx.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\CodeAnalyzer.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\CodeAnalyzer_arm64.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartApp.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartClass.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartDumper.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartField.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartFunction.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartLibrary.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartLoader.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartStub.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartThreadInfo.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\DartTypes.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Disassembler.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Disassembler_arm64.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\ElfHelper.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\FridaWriter.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\Util.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\VarValue.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\il.cpp.obj CMakeFiles\blutter_dartvm3.4.0-190.0.dev_android_arm64.dir\src\main.cpp.obj /out:blutter_dartvm3.4.0-190.0.dev_android_arm64.exe /implib:blutter_dartvm3.4.0-190.0.dev_android_arm64.lib /pdb:blutter_dartvm3.4.0-190.0.dev_android_arm64.pdb /version:0.0 /machine:x64 /INCREMENTAL:NO /subsystem:console /LTCG /OPT:REF /OPT:ICF D:\blutter-main\packages\lib\dartvm3.4.0-190.0.dev_android_arm64.lib D:\blutter-main\blutter\..\external\capstone\capstone_dll.lib D:\blutter-main\external\icu-windows\lib64\icuuc.lib kernel32.lib user32.lib gdi32.lib winspool.lib shell32.lib ole32.lib oleaut32.lib uuid.lib comdlg32.lib advapi32.lib /MANIFEST:EMBED,ID=1" failed (exit code 1120) with the following output:
dartvm3.4.0-190.0.dev_android_arm64.lib(unwinding_records_win.cc.obj) : error LNK2001: 无法解析的外部符号 __imp_RtlAddGrowableFunctionTable
dartvm3.4.0-190.0.dev_android_arm64.lib(unwinding_records_win.cc.obj) : error LNK2001: 无法解析的外部符号 __imp_RtlAddGrowableFunctionTable
dartvm3.4.0-190.0.dev_android_arm64.lib(unwinding_records_win.cc.obj) : error LNK2001: 无法解析的外部符号 __imp_RtlDeleteGrowableFunctionTable
dartvm3.4.0-190.0.dev_android_arm64.lib(unwinding_records_win.cc.obj) : error LNK2001: 无法解析的外部符号 __imp_RtlDeleteGrowableFunctionTable
blutter_dartvm3.4.0-190.0.dev_android_arm64.exe : fatal error LNK1120: 2 个无法解析的外部命令
ninja: build stopped: subcommand failed.
Traceback (most recent call last):
File "D:\blutter-main\blutter.py", line 168, in <module>
main(args.indir, args.outdir, args.rebuild, args.vs_sln, args.no_analysis)
File "D:\blutter-main\blutter.py", line 149, in main
cmake_blutter(blutter_name, dartlib_name, name_suffix, macros)
File "D:\blutter-main\blutter.py", line 92, in cmake_blutter
subprocess.run([NINJA_CMD], cwd=builddir, check=True)
File "C:\Users\Aar0n\AppData\Local\Programs\Python\Python310\lib\subprocess.py", line 526, in run
raise CalledProcessError(retcode, process.args,
subprocess.CalledProcessError: Command '['ninja']' returned non-zero exit status 1.
根据提示是两个"__imp"找不到,查了下是ntdll.lib里的,找到blutter根目录下的blutter文件夹里的cmakelists.txt,把里面的target_link_libraries(${BINNAME} ${DARTLIB} capstone)修改成target_link_libraries(${BINNAME} ${DARTLIB} capstone -l ntdll)即可完成正常编译
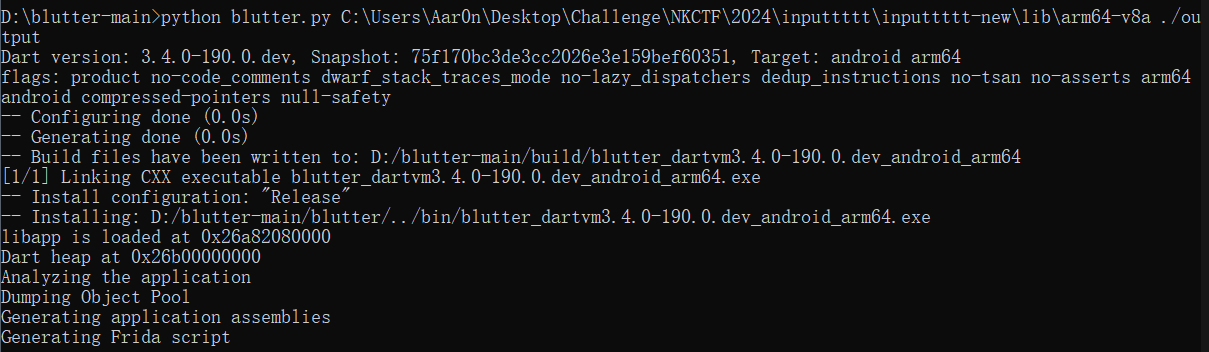
IDA恢复so符号表
我们选择Script File加载Blutter输出后的py文件
发现只能恢复一部分符号表
接下来使用Bindiff导入i64
在Matched Function中搜索inputtt
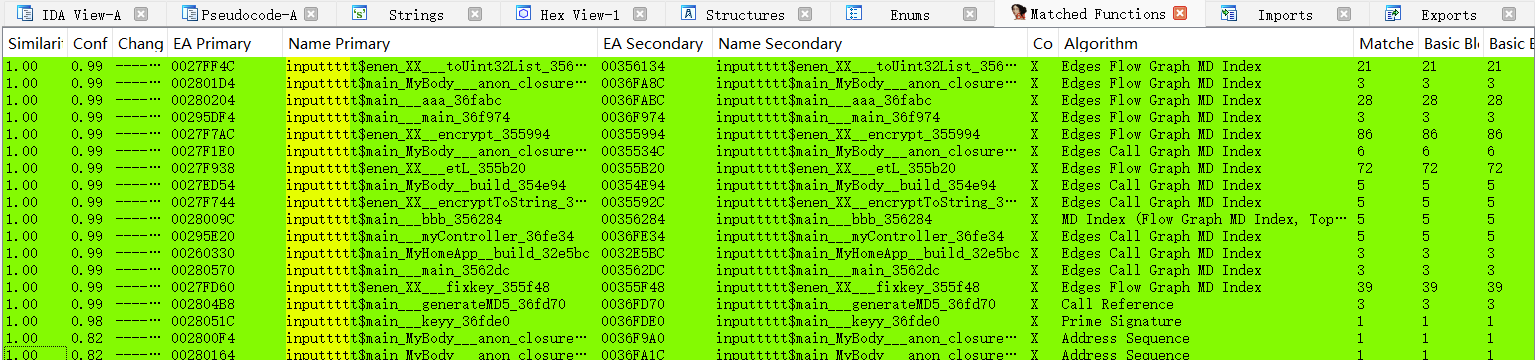
全选之后选择Import symbol/comment
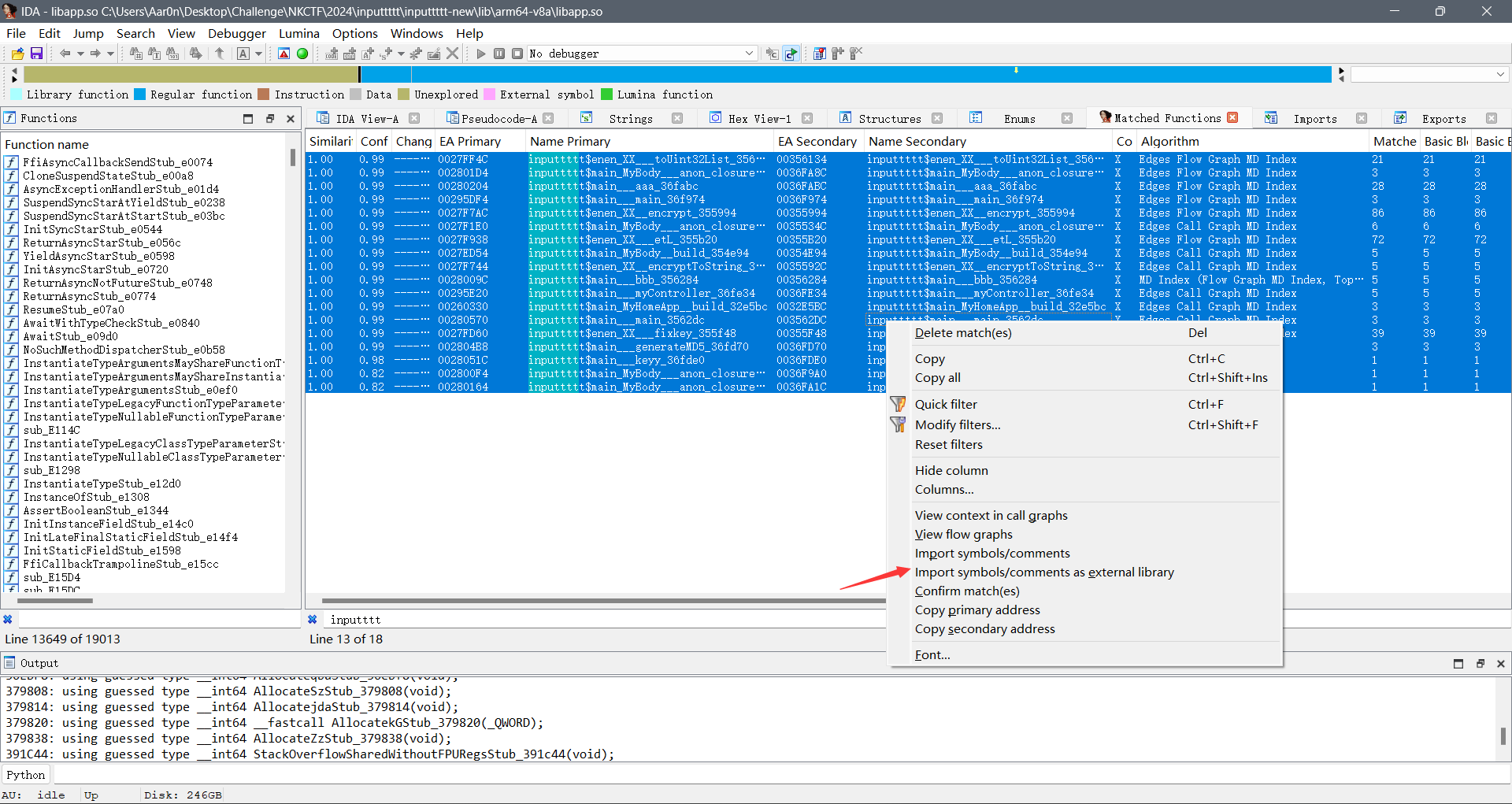
接下来就可以在左边的Function name中查找到inputtt的函数了
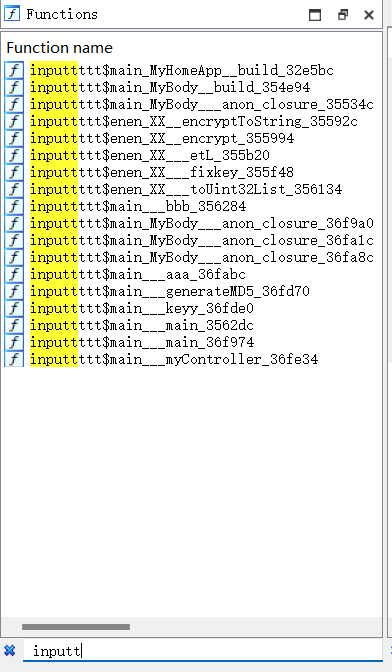
分析文件
导入符号表后在etL中找到了类似xxtea的地方
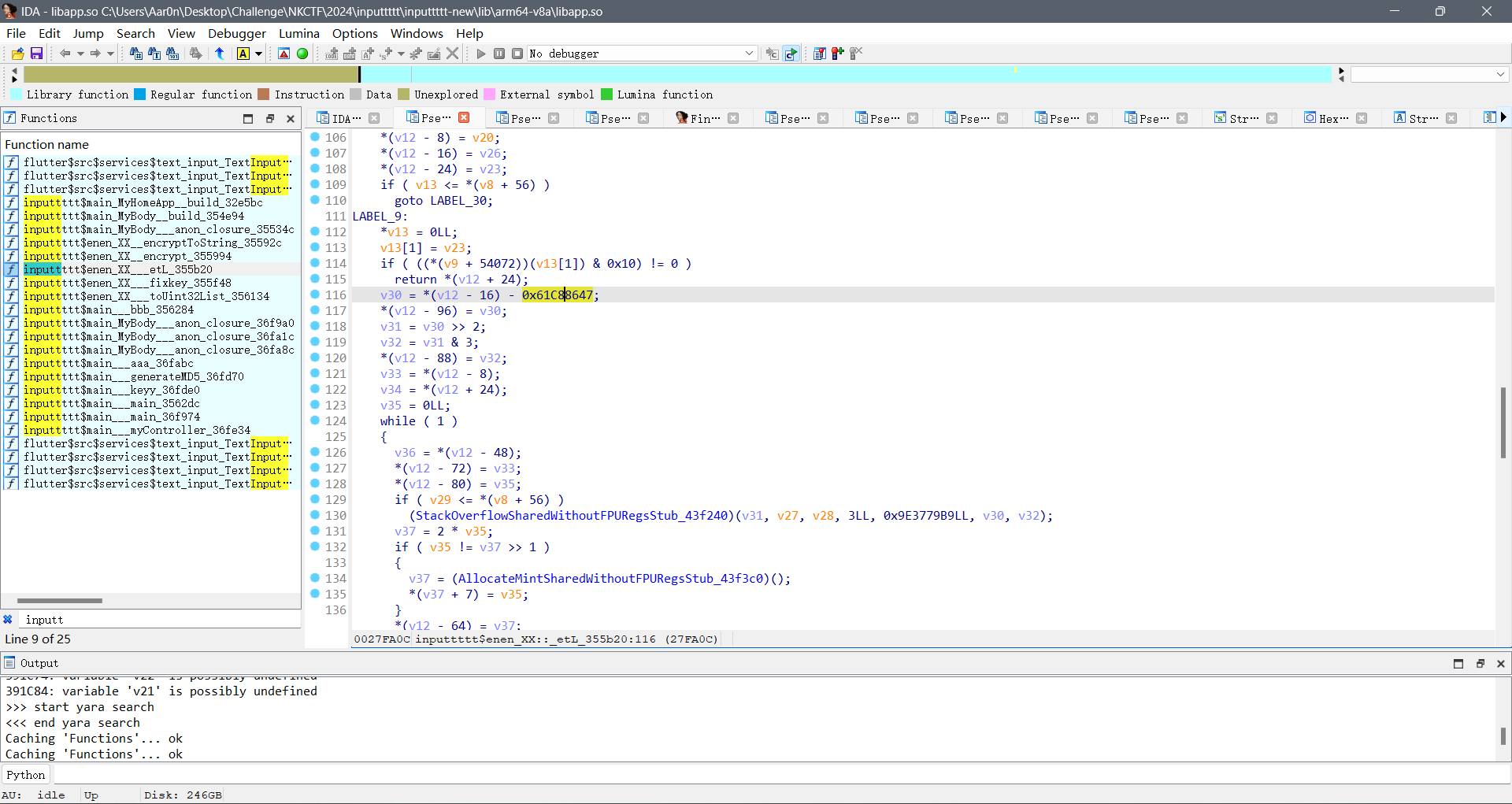
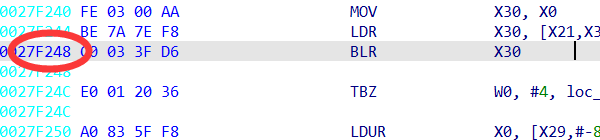
我们根据给的blutter_frida找到这个函数的首地址并在frida里修改地址
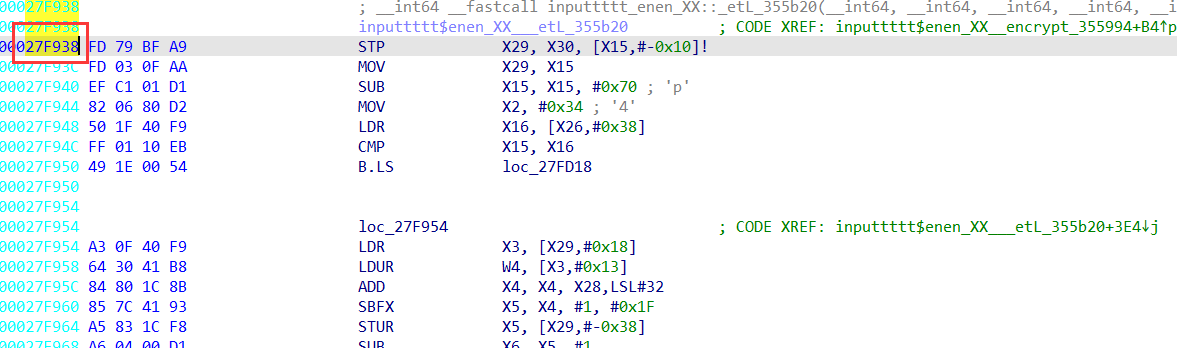
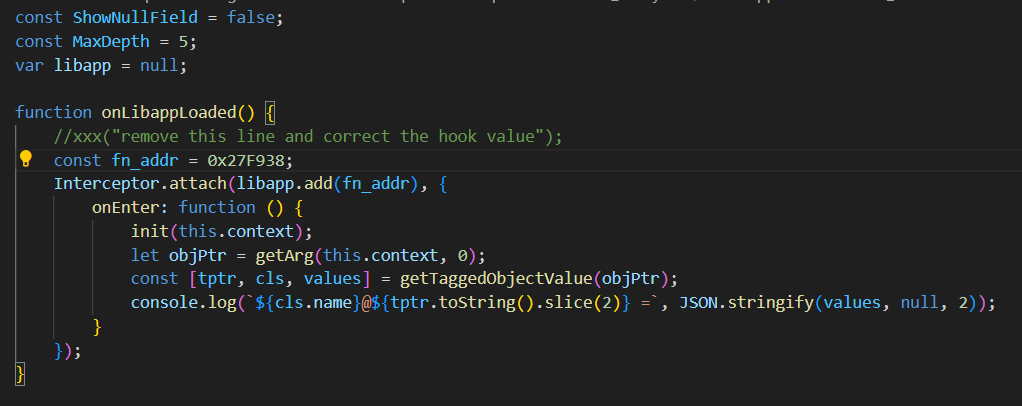
通过长按得到回显
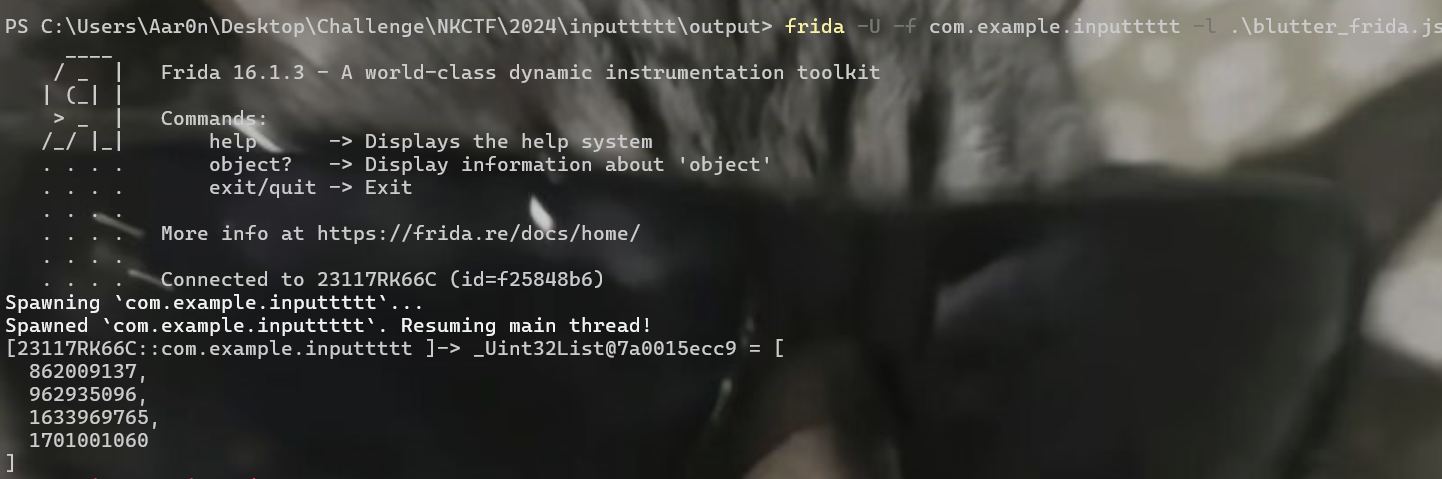
可以得到key为 17a389e9efdad7ce
#include <stdio.h>
#include <stdint.h>
int main() {
uint32_t values[] = {862009137, 962935096, 1633969765, 1701001060};
int num_values = sizeof(values) / sizeof(uint32_t);
for (int i = 0; i < num_values; i++) {
char* chars = (char*)&values[i];
printf("%c%c%c%c", chars[0], chars[1], chars[2], chars[3]);
}
return 0;
}
我们在encryptToString中向上交叉索引
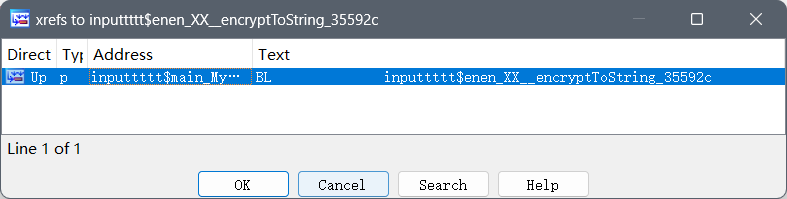
可以看到这个函数
我们在控制流中查看有两个分块,应该是判断正确错误的,并且最后有RET
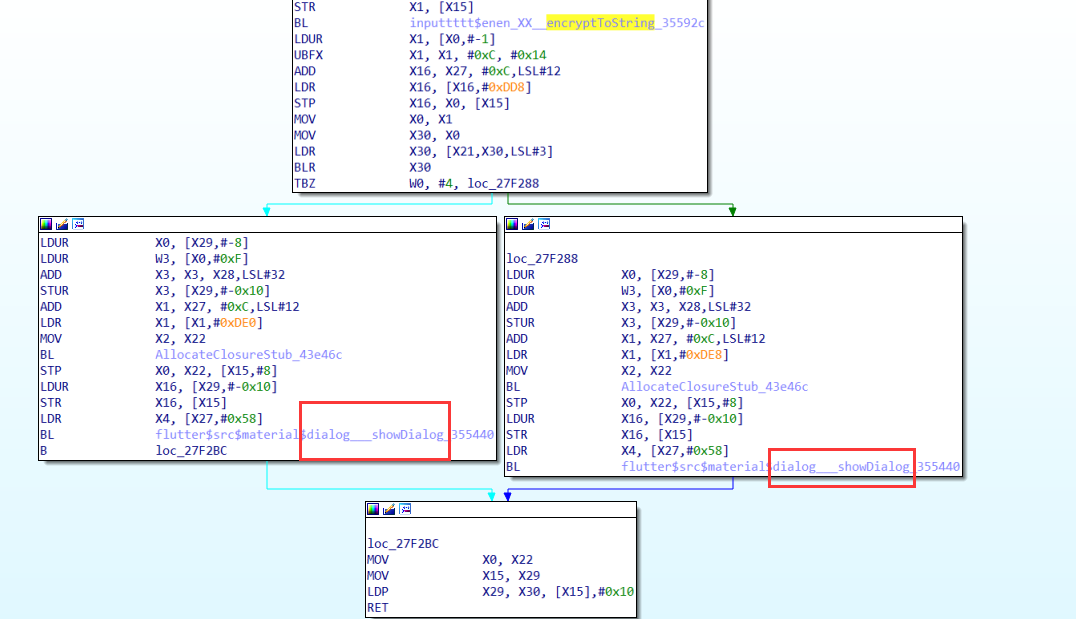
接下来直接用blutter_frida来hook这个比较的地址
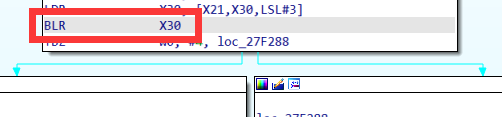
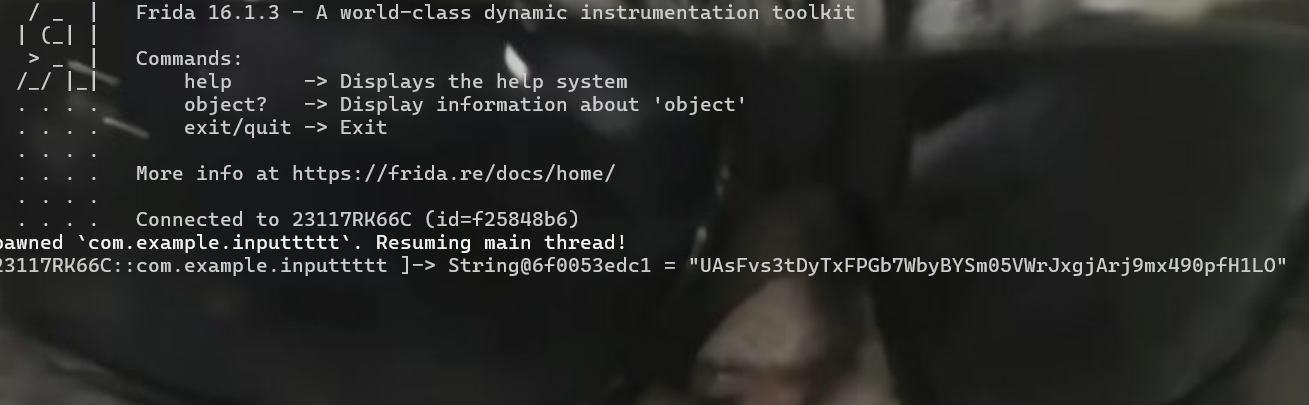
直接得到密文
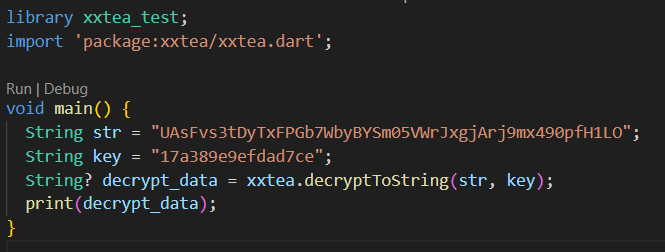
Github上有现成的XXTEA的dart版 clone下来在项目中
dart pub get
然后在vscode直接运行
或者cmd中使用
dart run .\main.dart
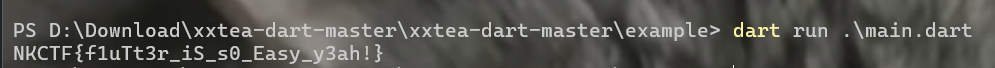
得到 NKCTF{f1uTt3r_iS_s0_Easy_y3ah!}